security analysis
To ensure safe and effective operation of IoT and security and reliability of services, scheme design must meet key security requirements. In this section, a comprehensive security evaluation of the proposed authentication scheme is performed, especially against common cyber-attacks in IoT, and compared with existing works with similar objectives. A comparison is shown in Table 1.
Table 1 Comparison of security attributes. Integrity
Data accuracy and tamper-proofing are key to ensuring the safe operation of smart factories. The accuracy of device credentials is directly related to trust and normal operation between devices. Tampering with this information can not only cause system failures but also pose security risks such as unauthorized access to devices, impacting productivity and data security. Therefore, ensuring data integrity is especially important.
In our proposed scheme, data integrity is guaranteed through multiple layers of security measures. First, data is stored and transmitted using AES symmetric encryption. This, combined with Hyperledger Fabric’s privilege control mechanisms, ensures that only authorized users and devices can access and modify data. Transactions are then signed using ECDSA digital signature technology to ensure that the data cannot be tampered with while in transit over the network. Additionally, transaction data is hashed using a hash function such as SHA-256 to provide additional integrity checks and ensure that data changes are detected in a timely manner.
mutual authentication
Mutual authentication is the foundation for devices in a smart factory to communicate securely. By establishing a trust relationship, devices can vouch for each other’s identity, preventing unauthorized access and potential security threats. Effective mutual authentication not only protects the security of data transmission, but also provides reliable collaboration between devices.
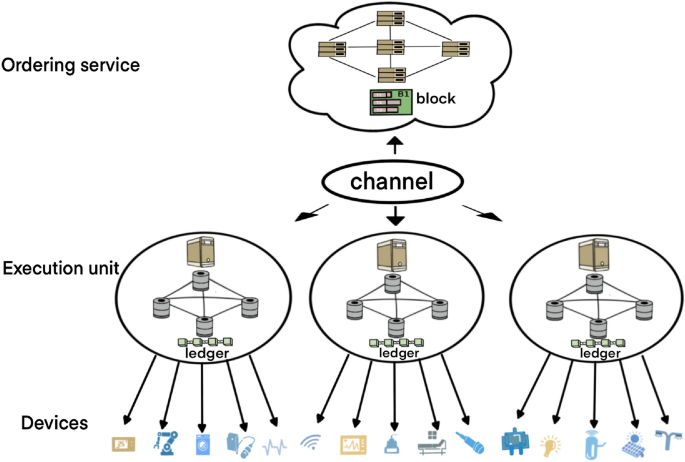
Each device holds a license digitally signed by a trusted authority and uses that license to authenticate itself to the blockchain network. Because of this, only valid devices can successfully complete authentication. Finally, information about the mutual authentication of the two devices is recorded on the blockchain ledger.
Scalability
Scalability faces many challenges in IIoT environments. As the number of devices proliferates, the complexity of managing and authenticating legitimate devices increases significantly. Traditional centralized authentication methods may not be able to efficiently handle large-scale device registration and authentication requests, leading to performance bottlenecks. Additionally, connecting many devices at the same time can congest the network, increase latency, and impact the reliability of real-time data transmission. At the same time, security and trust issues are becoming increasingly prominent, and illegal device access can threaten system security.
To address these challenges, this paper proposes to utilize blockchain technology to record device credentials. The decentralized nature of blockchain ensures tamperability of each device’s identity and efficiently handles large authentication requests through a consensus mechanism, increasing the scalability of the system. To address invalid device access issues, we establish an effective revocation mechanism to maintain system safety and reliability in a changing device environment.
Resistant to replay attacks
Resistance to replay attacks is an important measure to ensure the security of smart factory systems. An attacker could leverage the submitted transactions to send duplicate requests to the network, which not only leads to wasted resources but also poses significant security risks and affects the normal operation of the system. may give. Therefore, it is important to take effective protective measures.
In our scheme, each transaction includes a timestamp, effectively preventing replay attempts with the same or expired timestamp. At the same time, the unique transaction ID of transactions and the tamperability of the blockchain ensure the integrity and traceability of transaction history, preventing tampering and repeated attempts of submitted transactions. Combining these mechanisms can effectively resist replay attacks and protect system security and stability.
Resistant to man-in-the-middle (MITM) attacks
Resistance to man-in-the-middle (MITM) attacks is key to securing smart factory communications, as attackers can eavesdrop or tamper with information during communications, leading to data leaks and equipment manipulation. Therefore, it is important to ensure the confidentiality and integrity of communications.
Our scheme uses the TLS protocol to encrypt communication between nodes, which effectively prevents intermediaries from eavesdropping and tampering with transactions. Only a node with the corresponding private key can decrypt and authenticate the communication, thus ensuring secure transmission of information.
Resistance to impersonation attacks
Resistance to impersonation attacks is an important part of securing smart factories. Attackers may try to gain access to your system by pretending to be a legitimate device, which not only jeopardizes the security of your data but can also lead to equipment failure and production disruption. Therefore, it is important to ensure the authenticity of device IDs.
In our scheme, IIoT devices are authenticated using digital certificates and private keys. Each device has a unique digital certificate and private key issued and managed by a trusted CA. This mechanism ensures the uniqueness and authenticity of the device, effectively prevents attackers from imitating the device’s identity, and protects the security and reliability of the system.
Resistant to distributed denial of service (DDoS) attacks
Resistance to distributed denial of service (DDoS) attacks is a key strategy to ensure the successful operation of smart factories. Attackers consume system resources through a large number of requests, resulting in service interruptions or malfunctions. If the target device is the central node of a centralized system, its failure will have a significant impact on the entire system. Therefore, it is especially necessary to establish effective protection mechanisms.
Our proposed approach can effectively defend against DDoS attacks through mechanisms such as channel separation, load balancing, and high availability. Channel separation assigns different IoT devices to different channels, thereby limiting the impact of a DDoS attack to a specific channel without impacting the entire network. At the same time, load balancing and high availability maintain continuity of authentication services by allowing the network to evenly distribute traffic and quickly switch to a backup node in the event of an attack. This comprehensive architecture greatly increases the system’s resistance to DDoS attacks.
Cross-domain authentication and decentralization
Cross-domain authentication is an important means of ensuring secure cooperation between different organizations. As IoT devices and services continue to expand, trust relationships between multiple organizations become increasingly complex. Effective cross-domain authentication protects data and resources from the threat of unauthorized access by ensuring that only authenticated members can access the network.
In our scheme, cross-domain authentication manages user identities through certificate authorities and digital certificates to establish cross-domain trust. On the other hand, decentralization is reflected in decentralized network structures and consensus mechanisms, which avoid single points of failure and allow each node to enjoy equal status in validating transactions and maintaining the ledger. And the execution of smart contracts further enhances the application logic of decentralization. Together, these features ensure network security and stability and improve overall system reliability.
efficiency analysis
The number of ordering nodes and peer nodes both affect network performance, but their roles and points of influence are different. Ordering nodes are responsible for consensus, and increasing their number can make the network more resilient and prevent single points of failure, but it can also increase communication delays, which can affect overall processing speed. there is. Peer nodes are responsible for maintaining the ledger and running the chain code, and increasing the number of peer nodes increases parallelism and increases overall throughput. However, increasing the number of peer nodes increases data delivery time, which can affect transaction processing speed. Therefore, in some cases, performance optimization may focus on peer nodes.
To this end, we set up an experiment in which we deployed a blockchain network on multiple cloud servers, each running multiple peer nodes and ordering nodes, and observed the impact on system performance of varying the number of peer nodes. The various parameters of the experimental environment are listed in Table 2. Uses the Hyperledger Caliper performance testing framework. You can use it to stress test your Hyperledger fabric and print detailed performance metrics reports. In addition, we use Prometheus to continuously collect system resource usage during Caliper tests, giving you a comprehensive view of how your network performs under heavy load. We evaluated three different transaction requests (device registration, device authentication, and device revocation) and averaged the results. The experimental results are shown in Table 3.
Table 2 Experimental environment parameters. Table 3 Effect of number of peer nodes on performance.
Transaction latency is the time between when a user submits a transaction request and when the transaction is confirmed on the blockchain and written to the ledger. As can be seen from Table 3, the average transaction latency for the three transaction requests is relatively low at the beginning, but increases significantly with the number of nodes, especially after 20 nodes, the latency increases to 470 ms. . Ledger synchronization time is the time required to propagate and synchronize transaction data between multiple peer nodes and increases with the number of peer nodes. This indicates that synchronization of ledger data takes longer for more nodes. Throughput indicates the number of transactions that can be processed per second. As can be seen from Table 3, the average throughput for these three transaction requests peaks during node addition and levels off or even decreases slightly after 20 nodes. This indicates that too many nodes can cause performance bottlenecks. The resource consumption increases significantly with the number of peer nodes, especially when the number of nodes reaches 30, the CPU resource utilization reaches almost 100%.